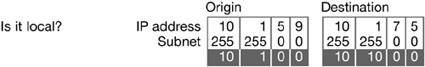
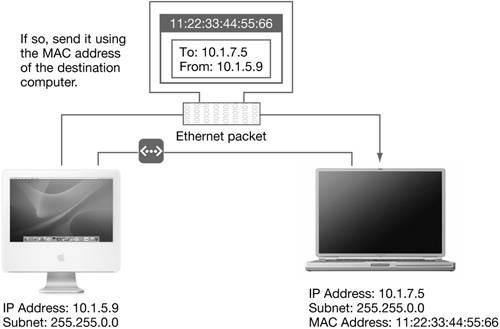
Understanding Networking ConceptsBefore you troubleshoot networking problems, you need to understand the basic concepts of how computers communicate, whether across the room or around the world. If every computer in the world could be connected to one single Ethernet network, your computer would be able to send data directly to every other computer. However, computers are actually linked to a collection of connected networks. The largest IP networks are made up of smaller networks. Large networks, which span a large logical area, are called wide area networks, or WANs. As networks become smaller and more specific to an audience, they are called local area networks, or LANs. Finally, LANs can be divided into physical or logical subnetworks or subnets. Although the distinction between LAN and WAN is arbitrary, you can think of a LAN as the devices in your network you can touch without leaving the building, and a WAN as all the network devices beyond the building's walls. Internet Protocol (IP) AddressIn order to communicate with computers across the various networks, each interface is assigned an Internet Protocol (IP) address. The IP address is not permanently fixed to an interface. Instead, the IP address assigned to an interface is based on the network to which the computer is connected. A network uses an IP address for its unique identification. The IP address in a TCP/IP packet encodes the information necessary to deliver the packet to the network through to the subnet of the recipient. An IPv4 address is a 32-bit number that is divided into four 8-bit parts called octets. These octets can have a value from 0 to 255. An example IP address is 10.1.45.186. Subnet MasksIn addition to the IP address, a computer also needs a subnet mask to help it identify the address range for the local network. Like the IP address, the subnet mask is a 32-bit number made up of four 8-bit octets. The local IP address range is determined by applying the subnet mask to the computer's IP address. The bits that are turned on in the subnet mask specify which bits of the IP address define the local address range. For example, a subnet mask of 255.255.255.0 applied to an address of 10.1.2.3 means the local address range is 10.1.2.0 to 10.1.2.255. Whenever a computer needs to send out a packet of data, it applies the subnet mask to the destination IP address to determine if the packet is to be sent to a computer on the local network. If the address is within the local IP address range, then the data is packaged and sent across the local network to the destination computer. Media Access Control (MAC) AddressA computer uses a network interface to connect to a network. Network interfaces are hardware devices that support various protocols for network communication. The most common type of network interface is Ethernet. By design, every Ethernet interface has a unique identifier called a Media Access Control (MAC) address, also referred to as an Ethernet address. These addresses are used in the MAC layer of the network to uniquely identify network ports. One or more IP addresses may be associated with a single MAC address, but MAC addresses are unique to each Ethernet interface. A MAC address is made up of a series of octets, much like an IP address, although different MAC addresses may have a different number of octets, and MAC addresses commonly incorporate alphabet characters in addition to numbers. Several other technologies use MAC addresses to uniquely identify devices, although not all of them use IP networking. For example, each Bluetooth device has a MAC address with six octets. You can see the MAC address for any device in System Profiler. When your computer sends data to another device on the local Ethernet network, the IP data, including the destination and origination IP addresses, are grouped into Ethernet packets. The Ethernet packets are then sent across the network using the MAC address. The destination device then extracts the IP data from the Ethernet packets and handles it appropriately. Sending Packets Over a WANA WAN is different than a LAN. In most cases, a WAN describes a connection that crosses network regions that you do not control. For example, you might be connecting to a remote web server in the simplest example, or you might have a WAN link between offices in two cities, or you might create a secure VPN connection across the Internet.
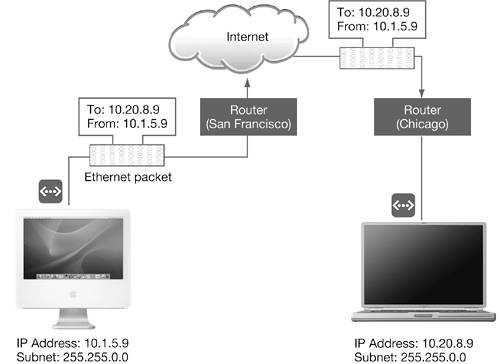
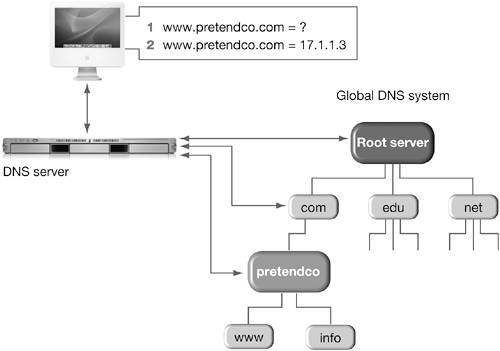
In the illustration above, you can see that packet transfer across a WAN is heavily managed. Our iMac G5 (at the left) applies the subnet mask to the destination address, and determines that the data is intended for a computer beyond our local network, so it sends the packet to its local San Francisco router. The router receives the network traffic and uses a routing table to determine where it should go. The San Francisco router is responsible for extracting the IP data and forwarding it, either directly to the destination computer if it is on a network connected to the router, or onto another router to be passed along to another network. It finds a routing table entry for the remote destination, and it connects to the Chicago router using the MAC address and sends the packet. The Chicago router checks the IP address for the packet, finds it in its routing table matched up with a MAC address on its local network, and delivers it to the PowerBook's network interface. NOTE This network diagram uses simple non-routable addresses for the purposes of this example. These addresses would not be used on most networks. Domain Name SystemTo make it easier for people to remember addresses, an IP address can have an associated name called a host name, such as www.pretendco.com or info.pretendco.com. The host name is associated with a domain name, such as pretendco.com. Because IP networking is based on the IP addresses, you need a method to translate the host name into its corresponding IP address. The entire system of host name and domain name mapping is called the Domain Name System (DNS). Dedicated hosts that provide DNS services are called DNS servers. Whenever your computer needs to look up an IP address that corresponds to a domain name, it consults the local DNS server.
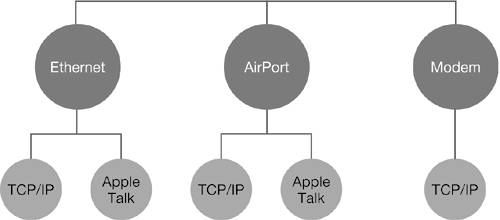
The problem is that the Internet is extremely large and constantly changing. New computers are added, servers are turned off, companies change names, and so forth. It would be impossible for your local DNS server to keep track of every possible domain name. Fortunately, it doesn't have to. Instead of needing to know every domain name and address combination, the DNS server looks up the address through a tiered server scheme. Your DNS server queries a series of DNS servers to find the IP for the given domain name. Once it has identified the IP address, it temporarily stores the address in a local cache so that the next time the server receives a request to look up the address, the server can quickly return it without having to look it up again. This is similar to when you need to call someone but do not know their phone number. If you need to call Chris Johnson at PretendCo, you would first call information to get PretendCo's main phone number. You would then call that number to get Chris's phone number. After you have Chris's phone number, you would store it in an address book to allow you to quickly recall it, instead of having to call PretendCo again to get it. Network Ports and ProtocolsA port (sometimes called a network interface) is an interface to similar devices within a LAN, or it serves as an interface to outside networks. Ethernet cards, modems, and AirPort cards are types of ports. Virtual ports, such as VPN, don't match directly to a physical interface. If you activate a port in Network preferences, you can configure the protocols available on that port. A protocol is a special set of rules that relate to communication between systems. In Network preferences, you can configure two protocols: TCP/IP and AppleTalk. TCP/IP protocol supports FTP, Server Message Blocks (SMB), and Apple Filing Protocol (AFP) network connections; AppleTalk is used for AFP discovery and printer connections on the network. Some ports only support certain protocols. For instance, the AppleTalk protocol is not supported over PPP modem connections.
NOTE The above diagram is not a comprehensive illustration of all ports and protocols available on a Macintosh computer. NOTE Beginning with Mac OS X 10.4, AFP is not supported over AppleTalk. AFP discovery over AppleTalk still is supported, but AFP uses IP to actually complete the connection. |